[PEGASUS-934] Escape user input when generating autocompelete list HTML to avoid XSS attacks #157
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
https://zendesk.atlassian.net/browse/PEGASUS-934
Context
With the fix, autocorrect HTML is rendered with sanitised user input:
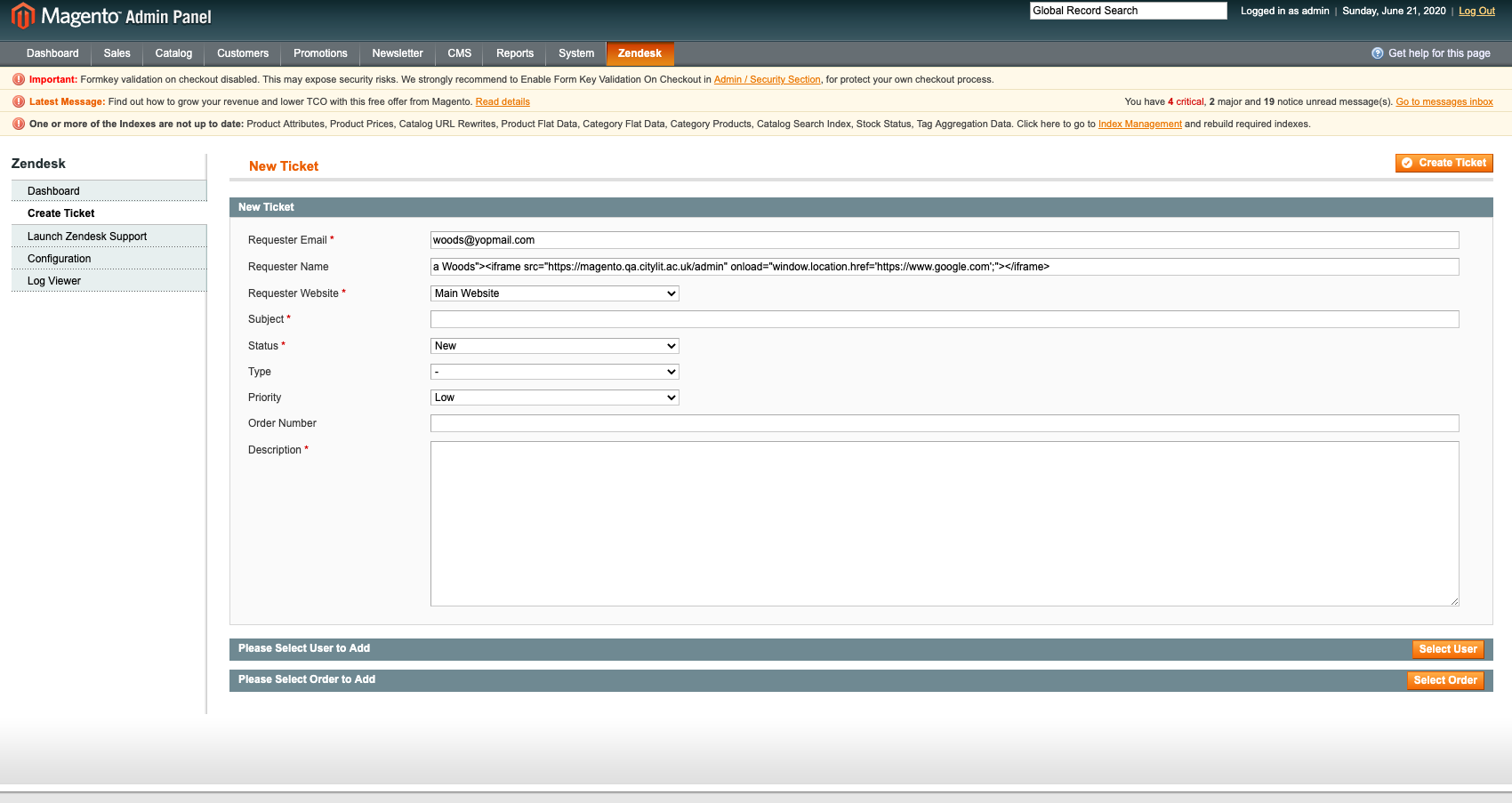
Note how the above page didn't execute the injected code but instead escaped it and rendered it.
Can test with https://github.com/zendesk/magento-k8s/pull/5